My thoughts are with those of you in Texas and neighboring states dealing with the ordeal of Hurricane Harvey.
While no amount of preparation could have prevented this horrendous event, preparedness…

A failure or accident brings your business to a sudden halt. How did it happen? What is at the root of the problem? What keeps it from happening again? Good detective work is needed -- but how do you go about it? In this new book, industry pioneer Fred Forck's seven-step cause analysis methodology guides you to the root of the incident, enabling you to act effectively to avoid loss of time, money, productivity, and quality.

Get your Business Continuity, Crisis Management and Resilience programs going with these powerful tools and templates for Businesses of all types and sizes – including Services, Manufacturing and Distribution!
Collect information and evaluate your business environment, identify and reduce risks, analyze business operations, analyze alternatives to respond to disruptions, develop a comprehensive Business Continuity Plan, and prepare for and respond to hazards-specific events with The Template for Comprehensive Business Continuity Management to Enhance Your Organization’s Resilience.
Get crisis-ready NOW! Learn from a master exactly what to do, what to say, when to say it, and when to do it while the whole world is watching: stop creating victims; communicate effectively with all stakeholders; prevent lawsuits; and reduce the negative impact of media hounds and activists. All supported by case studies and real-life examples, by trusted advisor to CEOs and practitioner/trainer named among the 100 Top Thought Leaders of 2013 by Trust Across America; profiled in Living Legends of American Public Relations; listed in Corporate Legal Times as one of “28 Experts to Call When All Hell Breaks Loose.”
Your CEO’s in handcuffs! Things are going downhill, fast! Your whole word is watching to see what you do next.

Have you begun to question traditional best practices in business continuity (BC)? Do you seem to be concentrating on documentation rather than preparedness? Compliance rather than recoverability? Do your efforts provide true business value? If you have these concerns, David Lindstedt and Mark Armour offer a solution in Adaptive Business Continuity: A New Approach. This ground-breaking new book provides a streamlined, realistic methodology to change BC dramatically.

I have rather mixed feelings about the devastating fire at the nearby Grenfell Tower. Having been brought up and worked most of my life in this part of London; I am even a Freeman of this great city. As a young boy I often visited family friends in who lived in Grenfell Road, long before the tower was built. The physical proximity and personal memories of the neighbourhood mean that I am keen to go over there and help. That then causes stress because of the appalling scene which prompts thoughts of the agonies experienced by thousands of people, many of whom we probably knew by sight. We do our weekly shopping in a nearby supermarket where we have probably chatted with some of them as we queued at the checkout.
The ruin now stands as a reminder of a tragedy which will never be forgotten in this part of the world. Indeed we still often think about the Great Fire of London that devastated our city 350 years ago. Yes, it caused devastation but it led to a better city with wider roads, a better layout and the foundation of our Fire Service.

Attend MIT Professional Education’s Crisis Management and Business Continuity course and prepare your organization for the inevitable. Offered since 2010, hundreds of participants have gained valuable insights and take-aways on business continuity, crisis management, disaster recovery, and crisis communications. Learn from MIT faculty and industry experts on MIT’s campus in Cambridge, MA July 24 – 28, 2017. Plus earn 3.3 Continuing Education Units (CEUs).

A crisis strikes out of the blue, at the time and place least expected. In a word, you’re Blindsided! According to Bruce T. Blythe, managing a crisis is an ultimate test of leadership, requiring leaders who inspire loyalty and trust as they rise to the occasion to meet the needs of people. Blythe shows you what it takes to be an effective and humane strategic crisis leader, a “crisis whisperer.”
While other books talk about crisis leadership, this one lands you in the middle of a fast-breaking crisis and demonstrates what a top-notch leader, a “crisis whisperer,” would say and do at every twist and turn. Blythe pulls up a chair and coaches you with real-world examples of what has worked — and not worked — in 30 years of experience with hundreds of companies just like yours. Some books tell you how to create a crisis response plan. Others tell you how to cope with the crisis as it takes place. Blythe does both.

New for Business Continuity Awareness Week!
You have the knowledge and skill to create a workable Business Continuity Management (BCM) program – but too often, your projects are stalled while you attempt to get the right information from the right person. Rachelle Loyear experienced these struggles for years before she successfully revamped and reinvented her company’s BCM program. In The Manager’s Guide to Simple, Strategic, Service-Oriented Business Continuity, she takes you through the practical steps to get your program back on track.
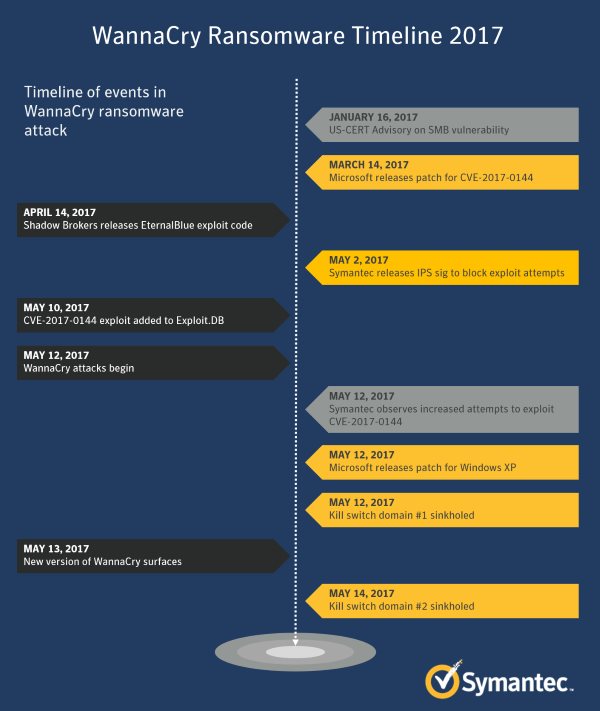
We all know we need to update our software, backup our critical data, install and maintain antimalware software and firewalls, manage robust contingency and recovery plans, not open funky emails, audit everything, blah blah blah. So what's wrong with us? Why don't we all do these things consistently?
I'd like to think that everything we have been lectured, reminded, scolded, chastised, and even ridiculed about in the way of protecting our digital assets is doable and reasonable, but face it – sometimes it's not. Costs, number of hours in the day, distractions, urgent priorities, sleep, other crises, get in the way. Or, to put it simply, we get lazy or "have better things to do."
