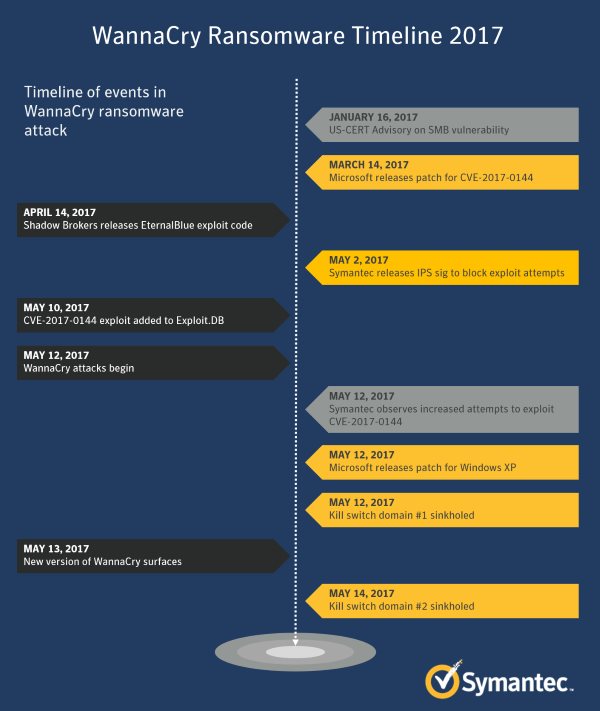
We all know we need to update our software, backup our critical data, install and maintain antimalware software and firewalls, manage robust contingency and recovery plans, not open funky emails, audit everything, blah blah blah. So what's wrong with us? Why don't we all do these things consistently?
I'd like to think that everything we have been lectured, reminded, scolded, chastised, and even ridiculed about in the way of protecting our digital assets is doable and reasonable, but face it – sometimes it's not. Costs, number of hours in the day, distractions, urgent priorities, sleep, other crises, get in the way. Or, to put it simply, we get lazy or "have better things to do."
Read More